Topics: Accounts Payable Automation, Accounts Payable Optimisation, Accounts Payable Process
Posted on April 04, 2022
Written By Divya Ramaswamy

Skim the news app or thumb through a newspaper, and chances are you’ll bump into a story or two about economic frauds or crime. Wherever there is money, there is a crime. Frauds are risks to which no business is immune. Even sophisticated, well-established tech giants like Facebook and Google have fallen prey to accounts payable fraud. Sadly, more than four in 10 U.K. businesses remain unaware of the risks associated with such crimes.
Accounts Payable frauds continue to occur across industries worldwide, despite the best efforts of financial officers and controllers. They disrupt businesses and can be notoriously challenging to detect, especially if you aren’t aware of the different types of AP frauds or the latest AP fraud detection & protection methods.
Accounts Payable (AP) departments are often perceived as easy prey and are thus prone to scams and malicious attacks. As payments are usually processed via AP departments, they become a prime target. But being hyperaware of your company’s business transactions and implementing several measures to curtail and respond to fraudulent activities can ensure the protection of your financial assets.
Accounts payable fraud refers to the common kind of deception or criminal activity targeting a business’s AP department involving outgoing payments. AP frauds can be committed internally by the employees, externally by vendors, both, or perhaps even by an outside party looking to access your business’s AP systems. AP fraud is all too common and causes hundreds of millions in losses.
Want to know more about Accounts Payable? Check out our ultimate guide and optimize payables for your business.
Read Our Free Guide
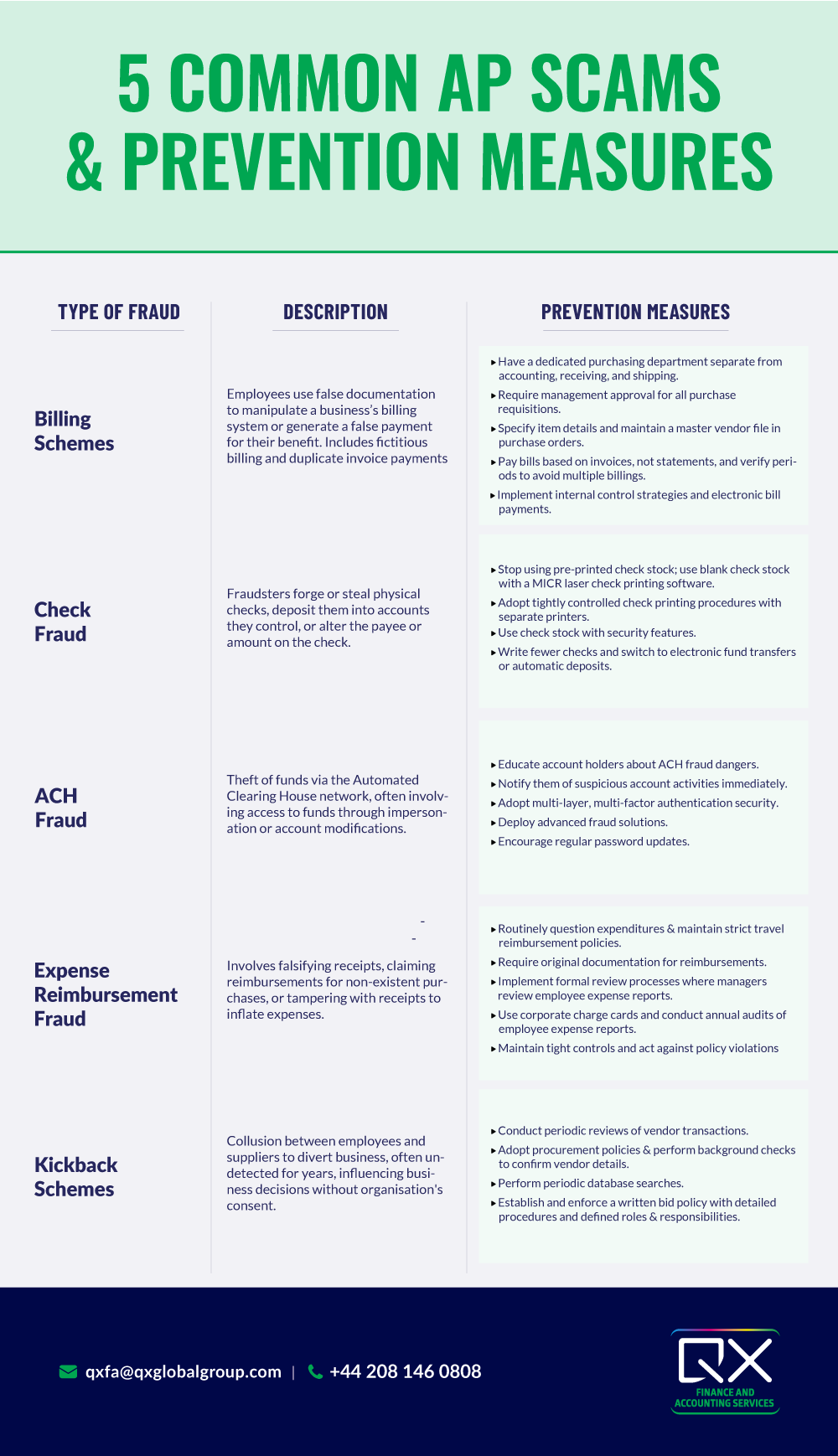
Let’s take a close look at the most common AP scams and understand what steps accounting teams can take to prevent them.
The most common type of AP fraud involves an employee using false documentation to manipulate a business’s billing system or generate a false payment for their benefit. Two common billing schemes include fictitious billing and duplicate invoice payments.
In the former, the fraudster creates a fictitious vendor that bills the company for payment, which is then diverted to the fraudster. A fake name and a post office box are all it takes to accomplish this. Whereas when it comes to the latter, the fraudster manipulates the vendor’s account, causing double payment and then diverts the amount to a bank account under their control.
This is one of the most frequently reported types of fraud where the fraudsters forge or steal physical checks and deposit them into accounts they control. Sometimes, they even change the company’s accounting system code to hide it. In some cases, the amount a check is made out for is adjusted, or the payee is changed.
Tech-savvy criminals can reproduce hundreds of realistic forged checks in just a matter of hours if they have access to basic corporate account information. Check fraud hits a company’s bottom line, but it also disrupts the business.
This refers to the theft of funds via the Automated Clearing House (ACH) financial transaction network. Many financial institutions use the ACH network to handle bill payments, direct deposits, and cash transfers. As common as this type of transaction is, it is also prone to fraud.
This type of AP fraud occurs when an employee or a hacker gain access to funds as they pass through an automated clearing house used to process electronic fund transfers. A routing number and a checking account number are all it takes to commit this fraud. The fraudsters also start engaging in vendor impersonation fraud, wherein they edit a current vendor profile to send payments to their account. ACH scammers target small to mid-sized companies and lower-income individuals who apply for loans frequently.
From falsifying receipts, claiming reimbursements for purchases that were never made or for complimentary rides or meals offered by hotels, submitting expenses that never happened, and producing fake or tampered receipts using online receipt makers or design tools, this type of AP fraud can be blatant.
Sometimes, these fraudsters collaborate with vendors to obtain receipts for purchases that never happened. Also, when organisations have expense policies that don’t require receipts for expenses under a certain amount, dishonest employees tend to take advantage of such a loophole and submit expense reports without receipts.
Safeguards to prevent this fraud:
This is one of the most damaging types of AP fraud, where employees and suppliers collaborate to influence a business decision without the organisation’s knowledge or consent. It can last years without detection, resulting in significant losses to victimised businesses. This type of fraud involves collusion between employees and vendors to divert business to the latter in exchange for money or value-based arrangements to the former.
As these schemes involve multiple employees, there is an increased opportunity to circumvent a company’s internal control procedures. And if the fraudster is a manager, they influence to facilitate it through the company’s normal accounting processes.
While whistle-blowers help detect most kickback schemes, companies can initiate the following processes:
As most businesses do not recoup their losses from fraud, it becomes even more crucial to prevent it beforehand. Closely watching for red flags can help identify and prevent fraud.
Benford’s Law, also known as the law of first digits, or the phenomenon of significant digits, is often applied when looking to identify fraud as it has to do with the expected occurrence of leading numbers in a dataset. It is the finding that the first digits of the records of the most varied sources do not display a uniform distribution but rather are arranged in such a way that the numeral one is the most frequent, followed by digits 2, 3, and so in a successively decreasing frequency down to 9.
Fraud examiners use this law to determine whether datasets are genuine. For instance, if an expense report lists 100 line items whose distribution of the first numeral differs significantly from the distribution outlined in this law, there is a reason to suspect that the employee could have forged it.

Image Credit: Wikipedia, https://en.wikipedia.org/wiki/Benford%27s_law#/media/File:Rozklad_benforda.svg
Are you a leader in detecting and preventing AP frauds? Or do you see areas of improvement that could be addressed as a matter of urgency? Either way, you ought to act now. Proactively conduct regular audits, watch for red flags, and check bank statements regularly. Conduct background checks, educate your employees on threats posed by phishing attempts and check & update the vendor master files regularly.
You can also partner with QX today to ensure security segregation of duties and protect your business from payment fraud. Our Accounts Payable outsourcing services have helped clients improve the entire payables process by delivering higher accuracy and decreased operation costs via process excellence, standardised AP practices, and strategic automation.
Are you curious to see how you can prevent fraud by outsourcing your Accounts Payable process? Contact us for a personalised consultation or call us on 0845 838 2592.
We hope you enjoyed reading this blog. If you want our team to help you optimise your payables process, improve supplier relationships, reduce costs and transform your business operations, just book a call.

Originally published Apr 04, 2022 02:04:15, updated Dec 27 2024
Topics: Accounts Payable Automation, Accounts Payable Optimisation, Accounts Payable Process